Simply secured browser. It perhaps is the best web browser powered by TOR. The UI is as simple as it gets. The browser together with DuckDuckGo makes it even more comfortable to browse without any worries about trackers, ads, etc. This is my go to browser from now on. Thanks to the developer for making this.
- Tor Browser will block browser plugins such as Flash, RealPlayer, QuickTime, and others: they can be manipulated into revealing your IP address. We do not recommend installing additional add-ons or plugins into Tor Browser.
- Tor Browser (Alpha) 10.5.14 Tor Browser is the only official mobile browser supported by the Tor Project, developers of the world's strongest tool for privacy and freedom online.
- The Tor Browser Bundle lets you use Tor on Windows, Mac OS X, or Linux without needing to install any software. Apple refreshes the iMac with Apple M1 and in a whole bunch of colors.

This guide outlines how to use the Tor Browser on macOS.
Tor Browser Apple M1 Pro
What is Tor? Anchor link
Tor is a volunteer-run service that provides both privacy and anonymity online by masking who you are and where you are connecting. The service also protects you from the Tor network itself—you can have good assurance that you’ll remain anonymous to other Tor users.
For people who might need occasional anonymity and privacy when accessing websites, Tor Browser provides a quick and easy way to use the Tor network.
Best Browser M1 Mac
The Tor Browser works just like a regular web browser. Web browsers are programs you use to view web sites. Examples include Chrome, Firefox, and Safari. Unlike other web browsers, though, the Tor Browser sends your communications through Tor, making it harder for people who are monitoring you to know exactly what you're doing online, and harder for people monitoring the sites you use to know where you're connecting from.
Jenkins is typically run as a standalone application in its own process with the built-in Java servlet container/application server (Jetty). Jenkins can also be run as a servlet in different Java servlet containers such as Apache Tomcat or GlassFish. However, instructions for setting up these types of installations are beyond the scope of. JENKINS CHEAT SHEET Jenkins is a software which allows you to do the continuous integration on your application/software lifecycle. It gets installed on the server where the central build will take place. Now lets understand its workflow. J e n k i n s FURTHERMORE: JenkinsTraining Commands in Jenkins: (URLs). This handy cheat sheet gives you all the essentials you need to know. Including how to install and manage Jenkins using Docker, pipeline concepts, job types, examples and the top Jenkins plugins for DevOps in 2021. Jenkins is an open source automation tool written in Java with plugins built for Continuous Integration purposes. Jenkins cheat sheet.
Keep in mind that only activities you do inside of Tor Browser itself will be anonymized. Having Tor Browser installed on your computer does not make things you do on the same computer using other software (such as your regular web browser) anonymous.
Getting Tor Browser Anchor link
Tor Browser Apple M1 Download
Open a browser like Firefox or Safari and go to:
If you are using a search engine to look for the Tor Browser, make sure that the URL is correct.
Do not use any other source, and if you are prompted to accept alternative HTTPS (SSL/TLS) security certificates, do not proceed.
Select the Apple download build icon:
If you are using Safari, the Tor Browser will start to download. In Firefox you will be asked whether you wish to open or save the file. For any browser, it is best to save the file first before proceeding. Select Save File and click the OK button.
This example shows Tor Browser Version 8.0.8, which was the most current version at the time this guide was published. There may be a more recent version of Tor Browser available for download by the time you read this, so please download and use the current version that Tor Project provides.
Installing Tor Browser Anchor link
After the download is complete, you might get an option to open the folder where the file was downloaded. The default location is the Downloads folder. Double-click on the file TorBrowser-8.0.8-osx64_en-US.dmg
macOS will now verify that the application hasn’t been tampered with. You may need to go to Settings > Security & Privacy to approve the download of a third-party application.
Next, a window will open asking you to install Tor Browser by dragging it to your applications folder. You may do so now.
Tor Browser is now installed in your applications folder.
Using Tor Browser Anchor link
To open Tor Browser for the first time, locate it in the Applications folder or in Launchpad.
After clicking on the Tor Browser icon, a window will open with a warning about the origin of the software. You should always take these warnings seriously and make sure you trust the software you want to install and that you got an authentic copy from the official site over a secure connection. Since you know what you want, and you know where to get the software, and the download was from the Tor Project's secure HTTPS site, click Open.
The first time Tor Browser starts, you'll get a window that allows you to modify some settings if necessary. You might have to come back and change some configuration settings, but go ahead and connect to the Tor network by clicking the Connect button. Cisco anyconnect vpn software download.
A new window will open with a gray bar that illustrates Tor Browser connecting to the Tor network.
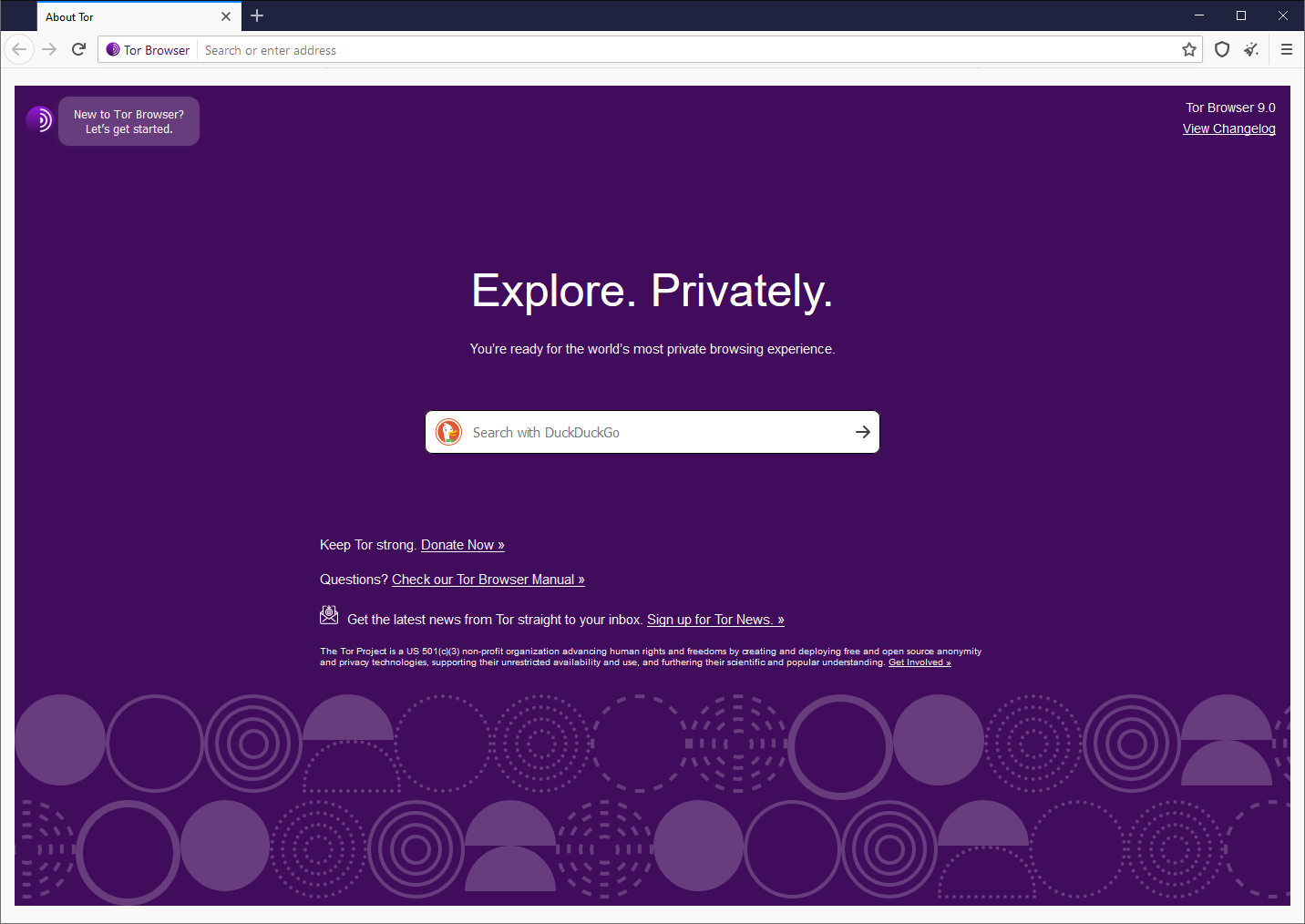
The first time Tor Browser starts, it might take a long time; but be patient, within a minute or two Tor Browser will open and congratulate you.
You will be greeted by the welcome screen.
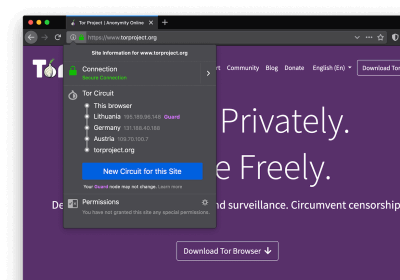
Click on the globe in the top left corner to review a tutorial on how Tor works.

The tutorial explains how Tor circuits work and how they allow you to browse privately online.
Some features of a normal web browser can make you vulnerable to man-in-the-middle attacks. Application for mac download torrent. Other features have previously had bugs in them that revealed users' identities. Turning the security slider to a high setting disables these features. This will make you safer from well-funded attackers who can interfere with your Internet connection or use new unknown bugs in these features. Unfortunately, turning off these features can make some websites unusable. The default low setting is fine for everyday privacy protection, but you can set it to high if you are worried about sophisticated attackers, or if you don't mind if some websites do not display correctly.
Finally, browsing with Tor is different in some ways from the normal browsing experience. We recommended reading these tips for properly browsing with the Tor Browser and retaining your anonymity.
You are now ready to browse the Internet anonymously with the Tor Browser.
